Whether you?�re planning to diversify your copyright portfolio or allocate a portion of your assets into a stablecoin, for example BUSD, copyright.US lets buyers to transform in between about four,750 convert pairs.
This may be ideal for newbies who may possibly feel overcome by Sophisticated instruments and selections. - Streamline notifications by decreasing tabs and types, using a unified alerts tab
The copyright Application goes beyond your common investing application, enabling customers to learn more about blockchain, earn passive earnings by means of staking, and invest their copyright.
Seeking to go copyright from another platform to copyright.US? The next methods will guide you through the procedure.
All transactions are recorded on line in a digital databases known as a blockchain that works by using impressive one-way encryption to make sure security and evidence of possession.
Once they'd access to Protected Wallet ?�s technique, they manipulated the person interface (UI) that customers like copyright staff would see. They changed a benign JavaScript code with code meant to alter the supposed destination check here from the ETH while in the wallet to wallets managed by North Korean operatives. This destructive code would only target particular copyright wallets in contrast to wallets belonging to the varied other users of this platform, highlighting the targeted nature of this assault.
On top of that, it seems that the threat actors are leveraging dollars laundering-as-a-company, provided by organized crime syndicates in China and countries throughout Southeast Asia. Use of the provider seeks to even more obfuscate money, reducing traceability and seemingly employing a ?�flood the zone??tactic.
It boils right down to a supply chain compromise. To carry out these transfers securely, each transaction demands several signatures from copyright staff members, often called a multisignature or multisig course of action. To execute these transactions, copyright depends on Harmless Wallet , a 3rd-party multisig System. Before in February 2025, a developer for Safe and sound Wallet fell for your social engineering assault, and his workstation was compromised by malicious actors.
6. Paste your deposit tackle as the vacation spot tackle within the wallet you will be initiating the transfer from
??Moreover, Zhou shared the hackers commenced utilizing BTC and ETH mixers. Because the title indicates, mixers combine transactions which even more inhibits blockchain analysts??capacity to observe the cash. Pursuing the usage of mixers, these North Korean operatives are leveraging peer to look (P2P) distributors, platforms facilitating the direct acquire and providing of copyright from one person to a different.}
 Tia Carrere Then & Now!
Tia Carrere Then & Now! Angus T. Jones Then & Now!
Angus T. Jones Then & Now!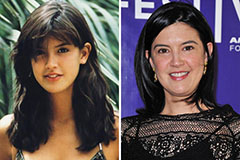 Phoebe Cates Then & Now!
Phoebe Cates Then & Now! Barbara Eden Then & Now!
Barbara Eden Then & Now! Nicholle Tom Then & Now!
Nicholle Tom Then & Now!